 BUSINESS CASE
BUSINESS CASE
According to IDC analytic company, by 2015 number of employees using mobile devices (notebooks, ultrabooks and tablet computers) for their daily work will have reached 37.2 per cent. It is mainly results from BYOD (Bring Your Own Device) policy being introduced in many companies. According to this policy employees can use their own mobile computers as corporate ones. Surely using mobile devices as primary ones has its own advantages but makes IT-infrastructure much more vulnerable. Research carried out by TrustWave company confirms high risks of mobile devices use:
- 90% of devices do not have operating system updates installed.
- 46% of users of mobile devices allow third parties to use them
- 37% of mobile devices do not have lock code on system logon
- 48% of users connect mobile devices to unsecured public networks
- 50% of employees install recreational software and other riskware to corporate mobile computers.
What risks can IT-infrastructure face in this context?
Interception of insecure network traffic
When your employees remotely connect to corporate network via unsecured network connection (generally via wireless hotspots in airports, hotels and other public places), they potentially begin to share all transferred data including business critical data with adversaries. This way of network attack is called Man-in-the-Middle. The name shows that a mere locating near the source of unprotected traffic and intercepting the traffic is enough for an adversary. History of cyber-crimes includes a lot of cases when due to unprotected network traffic adversaries had stolen dozens of billions dollars from companies. One can just remember histories happened to TJ Maxx and Lowe's companies to realize importance and necessity of secure remote connection to corporate network.
Vulnerabilities in operating system and application software
Updates for OS and application software are required first of all to remove discovered vulnerabilities which may have negative impact on IT-infrastructure security. Recently the term “Zero-Day Attack” is being heard more and more frequently. Attacks vector is firstly directed to the computers, where operating system was not updated in time and there are vulnerabilities supposed by adversary. One of the most awful “zero-day attacks” was in 2010 when internet-worm Stuxnet attacked computer systems in 19 countries that resulted in great financial losses of companies, IT-infrastructures of which were infected. When speaking about mobile computers one should bear in mind that they get update packs less often than workstations being continuously connected to enterprise network. Therefore mobile devices are in risk zone and potentially have riskware which can be distributed to the whole enterprise IT-infrastructure during remote connection and result in failures of different services. To reduce risk of such incidents to the greatest extent it is necessary to carry out “health monitoring” of mobile devices as early as connecting to enterprise network.
Unsecure publication of network applications and services
A special problem of publication of web-applications, portals and other web-resources to the Internet is keeping balance between security on one side and handy functionality of the resource on the other side. Generally this problem is solved by special network DMZ-zone where only the services that should be available to users from the Internet are located.
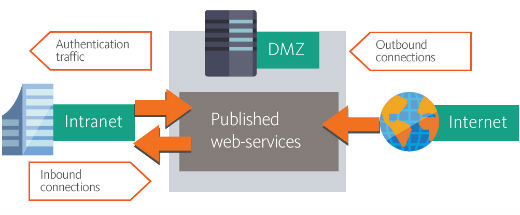
Moreover interaction of these services with intranet should be maximally limited to avoid creating potential vulnerability in the edge of corporate network. It is mostly important when web-resource authenticates users because traffic of authentication process carries critical information which can be used by adversaries.
This risk can be significantly reduced in case when authentication process proceeds directly in DMZ zone. In this case additional network sockets for authentication traffic between DMZ zone and intranet are not required. Additional advantage is capability to specify users and groups, authentication data of which will be stored in DMZ zone.
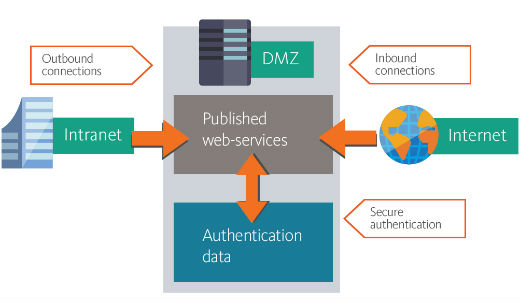
By choosing this solution you provide IT-infrastructure of your company with technologies which considerably increase security level of network connections, make remote network connections easier and handier for company’s employees and reduce risks related to unauthorized getting critical business information by adversaries during remote access to corporate network.
